Note: You don’t need any other WordPress Security guide if you follow all the steps mentioned in this guide.
Originally created for bloggers, WordPress has become a widely-used platform for website development and content management due to its ease of use, versatility, and reliability, making it an ideal choice for businesses of all sizes.
As WordPress websites and their data become more accessible due to their rising popularity, it is essential to guarantee that your sites are adequately protected with robust security measures in order to protect your data and that of your client. With improved security, you can expect improved performance, better outcomes, and greater peace of mind.
WordPress websites have historically been vulnerable to hacking, and if one fails to secure their blog adequately, they are at risk of being successfully attacked by a professional hacker. I have seen this happen to even highly experienced bloggers, so it is critical to take proper precautions.
Usually, a hacker is looking for vulnerable installations of WordPress using different tools. When it finds a vulnerable site, they exploit it to access the blog and insert links to various ill-reputed sites. This technique is an effort to use your blog to increase those sites’ Google PageRank scores (Nowadays, it’s called Domain Authority and Page Authority).
Despite two major security breaches of WordPress being reported in recent years, WordPress can become as secure as other Content Management Systems, such as Drupal and Magento, with the responsibility lying with website owners and maintenance service providers. To aid in this, WordPress has provided a Security whitepaper. However, it is ultimately up to the website owner to ensure their WordPress site remains secure by following the recommended steps.
This in-depth WordPress security guide is divided into six central portions.
- Understanding The Types of Security Risks
- Precautionary Measures To Prevent Hacking
- Webhosting and Security
- Two Factor Plugins
- WordPress Plugins For Blog Security
- What Steps should be taken if being hacked?
Types of Security Risks
The attacks to defend your WordPress installations are different in nature but not of the same severity. Let’s see the most common:
- Bruteforce login attempts: BruteForce is a common technique that aims to log in on the WordPress platform to take data and administration capabilities. It is not easy to create an attack, but now the possibility of using low-cost resources has increased the possibility that brute force is chosen to access our blog.
- SPAM in the comments: One of the most common attacks for blogs that do not use any protection technique, the bots enter thousands of comments in the post at a time without leaving the admin time to remove them, thus creating confusion and failures in the WordPress platform.
- Vulnerability of old versions and plugins: to have installed an older version of WordPress can be the best way to be attacked; many bugs are now known and have many exploits available for use. Same for the recently updated plugins representing a possible security flaw with time.
- SQL injection: although reduced compared to the past, this attack method is the most dangerous. The entry form can provide access to sensitive information and may allow the modification of database information.
There are specific solutions for these types of attacks to be implemented through plugins or settings that allow you to decrease the likelihood of being hacked. Most often, the attacks point to dozens of machines hosted by the same hosting provider and can lead to very automated binding systems.
It is also useful to consider the protection techniques their hosting providers apply; many providers now provide hosting solutions for CMS, thus making safety easier because the servers are already set for this specific CMS.
Let’s take a look at how we can protect our WordPress site by taking these steps.
1. Limit Login Attempts
WordPress offers unlimited turns to try to log in, which makes it vulnerable to Brute Force attacks. Using WAFcan solve this issue automatically. But, if you are not using WAF, you can use plugins like Login LockDown and others.

Blog security is the most important thing that we bloggers have to always keep in mind. There are always online threats out there, hackers, and most of all, idiots who are jealous of our blog’s success and try to sabotage it in some sort of way. This is why we must take security very seriously and make sure we have a killer setup. One thing to always do is limit login attempts to help combat these spammers who use automated software to register on multiple blogs to submit spam comments or spammy blog posts.
If you have money to invest in security now, I would strongly suggest using the iThemes Security Pro plugin. If not, follow this blog post and blog for many security tips.
For this reason, this is why the default membership role you should select should always be set to Contributor.
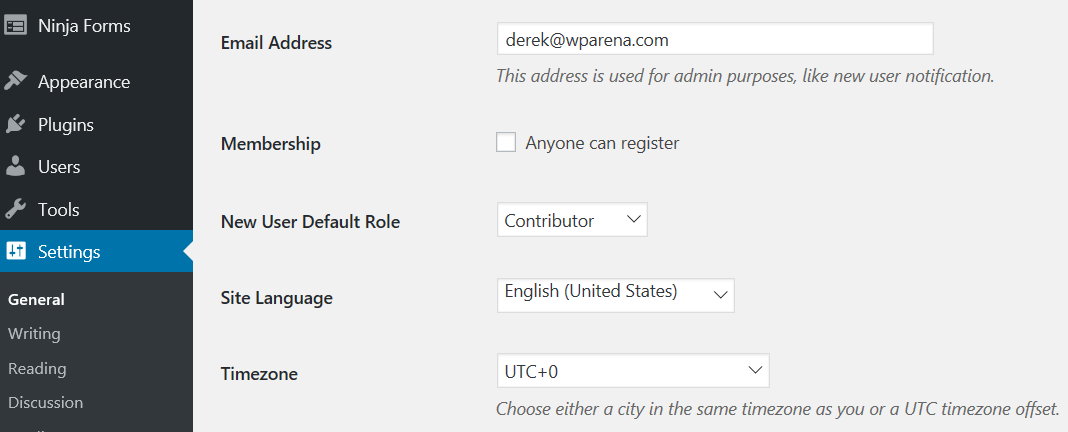
A contributor can only submit a blog post for review by selecting and cannot publish them. This stops unwanted blog posts from going live if you, the admin, or hired staff must read blog posts before they go live. This is one setting I commonly notice on brand-new blog installs with novice bloggers.
Let’s turn back to secure the login form from bad actors. The one plugin I found to be effective and is free is the Limit Login Attempts plugin.
What this plugin basically does is that it limits the login attempts. Let’s say someone is trying to login into your admin account using the “admin” username in which you should never use for your login username and is trying to get into your account. After x amount of bad login attempts, they basically blocked for x months or forever from trying to login again. You set the rules.
You can block IP’s altogether if you come across a list of spammers someone posted on a blog elsewhere. Don’t forget to whitelist your own IP and your staff so they don’t get blocked by accident.
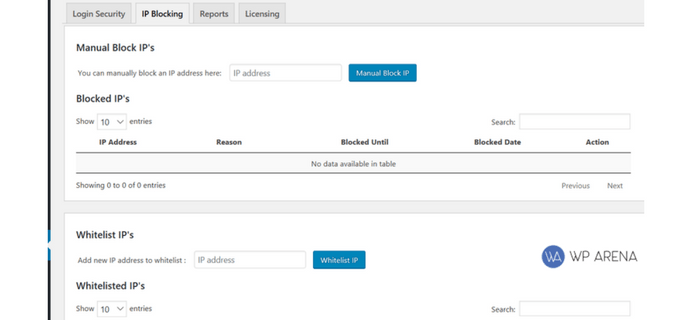
The reporting feature is to look at reports. You should constantly check these to see what’s going on and figure out if you have to block an IP or not.
Give Limit Login Attempts a try to let me know if this has resolved any issues for you.
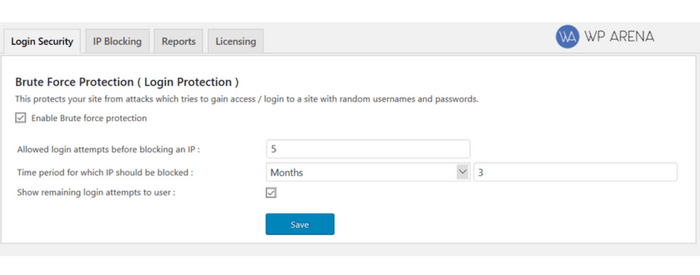
2. Activate WordPress Brute Force Protection
Activating brute force protection is another way to protect the website from potential brute force attacks. We suggest you use a protection service covering local and network brute force.
3. Don’t enable login hints
By default, WordPress login tells you if you enter the wrong password or username with suitable prompts. This works as an aid for hackers when trying attacks like brute force to hack into your account. There is a function.php file where you can disable these prompts and improve security.
4. Make Sure to Update As Soon As Possible
WordPress releases regular updates that often include security patch-ups. So, try not to miss the updates. Regularly updating WordPress can solve various security issues automatically.
With the development of WordPress, security issues are also increasing, so, first of all, make sure that you’re running the most up-to-date and secure version, and upgrade to the latest release as soon as you can. The outdated version can support malicious attacks and can increase the vulnerability to hacker attempts. Most WordPress security failures occur when a user is running an outdated version of WordPress on his website.
The latest updates often come out with the efforts of the core developers. All you have to do is grab the opportunity. You can only avail of these facilities if you keep your site updated to its latest version. This way, your site will be automatically protected from external viruses.
Those WordPress updates appear often, and you might find them annoying, but you must install them as soon as they appear. After all, WordPress is continually updated for a reason, often to fix bugs and provide security enhancements. If you stick with an older version, those lapses in security will still exist within the code.
Security updates apply automatically, but some major releases need to be updated manually by going to their respective pages. So if you don’t take time for these updates, you might leave your site prone to attack from hackers.
5. Keep WordPress, Themes, and Plugins Updated
Site administrators will be notified when new WordPress updates are available, and it’s essential to apply these as soon as possible. Updates usually contain important security patches for newly identified weak points or bugs.
WordPress updates can be set to download automatically as they’re released. Automatic updates are ideal, as they can install instantly. The same goes for plugins and themes, though these might have to be checked and updated manually depending on the setup’s plugins.
6. Disable file editing
WordPress has a built-in code editor that helps users edit plugins and themes directly from the admin area. If your site is compromised, then this feature could prove as fatal. We recommend you add the following code in the wp-config.php file to disable file editing-
// Disallow file edit define( 'DISALLOW_FILE_EDIT', true ); Disable PHP File extension Disabling PHP extension is also advantageous. To do so, paste the following code in a notepad and save it as .htaccess. Then upload it to /wp-content/uploads/ folders. <Files *.php> deny from all </Files>
7. Password Strength
Could you imagine having all of your hard work undone by a weak password? Well, too many website owners succumb to this problem, even though the fix is an easy one. All you need to do is produce a password with the right mix of letters, numbers, and symbols. Plus, you can even use a website such as a password generator to make a secure password instantly.
Directly at the beginning of the installation, you are asked to enter the database access data. Again, there are no passwords that are too strong. This also applies to any user accounts that are subsequently created. If you allow users to register later, plugins that only allow strong passwords (e.g., DF5kysdZS66) are advisable.
This is of utmost importance that you keep a secure password for your website; this way; you are giving the hacker a tough time intruding on your site.
If you keep simple passwords like “your name” or “12345,” it will be easy for the hackers to guess it and log in to your site. Hackers are very good at understanding the human psyche, so if you think that some simple words like “password” could not be guessed, DON’T take the risk. Once hacked, you might lose your account as the hacker may immediately change the password and start adding malware to your site.
So this is a rule of thumb; always choose some complicated yet related password that you are sure that no one other than you can easily break down. It’s recommended your password contains uppercase letters, lower case letters as well as random numbers so that your hacker is given some tough time.
You don’t necessarily need a long password, just a unique one that only YOU can easily relate to.
8. Use SSL Certificate
SSL/TLS certificate is important because they keep the business website secure. Even according to the survey, those websites that don’t use SSL certificates are the easiest target.
The importance of SSL certificates is not new. It is one of the best methods to secure your website, and with cheap wildcard SSL options available in the market, it has become more affordable. SSL ensures that the data is secure from hackers while it is on the move. The data is encrypted before any data transfer occurs between the server and the browser and prevents data breaches. The users’ credentials may be extremely critical, like passwords, and transactional data, and making sure they are sure is of utmost priority. Hence SSL certificate is one of the methods that must be used to improve security.
Secure Socket Layer certificate is used by many websites like Google, Facebook, and Twitter. Instead of HTTP in the link, you may see HTTPS, indicating the SSL certification. This ensures that the connection is encrypted and safe to use.
So if your site involves entering usernames or passwords, you must use an SSL certificate to secure everyone’s personal information.
Easy HTTPS Redirection and Verve SSL are two good SSL plugins currently available.
9. Use Trusted WordPress Themes
Many directories are full of various themes and plugins which you can use for your WordPress site. However, not all of the themes can be trusted. The entire themes list is created independently. Some top-notch banks contain themes, all well approved by volunteers, but you never know if one of them has any malicious code which might cause significant WordPress malfunction.
So much so that these faulty plugins might contain some security loopholes. Hence hackers can easily intrude on your site through these plugins.
The best you can do is always check reviews from people before downloading a theme for your site. Ensure the site offering you that theme directory is known for its excellence, like WPMU DEV. Search for reviews from volunteers and then choose the best.
- ThemeForest – Themeforest is probably currently the most popular premium WordPress theme marketplace. Created by the great team over at Envato, they have over 6,000 WordPress themes that cover a wide variety of styles and features.
- Elegant Themes – Join 282,273 Happy Customers And Get Access To Elegant Themes’ Entire Collection Of 87 Beautiful Themes For The Price Of One.
Choosing a free WordPress theme can be a tough job. Especially if you’re a beginner, when searching the web for free themes outside the WordPress directory, be aware that the popularity, open code, and ease of use in making WordPress themes are attractive to others who can make your web server could become part of a zombie army of machines participating in a Distributed Denial of Service (DDoS) attack on some other website. Still, some may contain malicious code in there. Especially if you download it from random websites and not from WordPress.org, it can be used in a phishing scheme to mine passwords and other personal information from your visitors—unbeknown to them.
So always select themes that are available through the WordPress Free Themes Directory. At least they follow the community’s rules. Although themes are collections of programming code and, thus, can have bugs.
Don’t be afraid to ask the developer questions before installing a theme from outside the traditional channels.
Visit the developer’s site, and check the WordPress.org forums to know the developer’s reputation.
– WordPress Antivirus
This plugin is another handy plug-in, and it scans your theme directory. It specifically detected the WordPress permalink back door, a malicious malware for WordPress, and used it to access the database. This plug-in shows green if your file is out of danger and red if your file may be in trouble.
10. Be careful with Plugins
Plugins are an integral part of WordPress websites. WordPress contains thousands in its repository; other websites online from where plugins can be downloaded. Before downloading a plugin for your website, it is essential to verify its authenticity. Look for reviews; consider how often the author of the plugin responds to queries. Finally, install a trusted security plugin to maintain the website’s security, look for malware, and monitor it.
11. Review WordPress Themes and Plugins Regularly
Plugins and themes can threaten websites through bugs, thus opening websites up to exploitation. Developers also regularly abandon plugins and themes, making them obsolete and dangerous.
Set out a couple of times a year to review themes and plugins by checking whether they’re still supported and receive regular updates.
12. Never keep a Default Username
To maintain security, it is clever to change the default username “admin.” WordPress will let you change the username by default. So, you can directly change the username or use a special plugin to do so. However, since admin is a default username, not changing the username makes it easier for brute-force attacks.
If you create a first user, you should name it more cryptic than “admin” or “administrator.” These names are often used for this kind of user account and are therefore easy to guess. Suppose you want to go one step further. In that case, you should also adjust the user ID in the database accordingly, since the first administrator is assigned “1” as the user ID, which also plays into the cards of a hacker regardless of the choice of name. This will also make sure to reject people that will use pirate proxies to change their IP
Ensure your administrator username is not “admin,” root, owner or administrator, or any other word that suggests that this may be the administrator’s credentials. This is a fundamental tip that is often overlooked, not just for WordPress but for all websites in general. Making it evident that a username-password combination belongs to the admin makes the hacker’s job easier. They know precisely which credentials to crack to get admin access to the entire system, which can cause havoc.
Once your site is created, the username is already set to “admin.” In this case, it’s easier for hackers to attack your site as you have already provided the username. Now they only have to guess the password. So give them some tough luck and set a related username. Hacker is now one extra step behind you once you have manually changed the username.
Change the username “admin” in Mysql, run this query in your MySQL admin
update wp-users set user_login=’newuser’ where user_login=’admin’;
or create a new /unique account with administrator privileges.
- Create a new account with a unique username
- Assign as an administrator role
- Log out and log back in with a New Account
- Delete admin account
Be careful while confirming the Deleting of the admin account because it will ask you to delete all posts and links related to that account.
13. Do not create a customer login as an administrator
If other users need to be generated/created, you should only assign the administrator status in extreme cases. Here applies: Too many cooks spoil the broth, and to all abundance, the security suffers likewise.
It is more advisable to assign the status of the “editor” to customers. The rights are more than sufficient for everyday use, and the risks are severely limited. If the rights management within WordPress needs to be refined accordingly, plug-ins such as “Members” can create their own roles with customized user rights.
14. Use a VPN When Logging Into the Site
While admins can take every precaution to secure their website, all of that is moot if their devices and network aren’t secure. Hackers will use any entry point to work their way into the system through an infected device or an unsecured network.
There are plenty of ways to add extra layers of security to devices, and that’s undeniably important but not the focus here. So make sure to consult cybersecurity resources and set up policies regarding device security. As for network security, VPNs are the way to go.
What is a VPN? It’s a tool that creates a safe and encrypted connection between your device and the destination on the web. This protects against man-in-the-middle and SSL stripping attacks and against hackers identifying admins based on their IPs.
15. Use The Cloud
Expanding on the previous point makes a lot of sense to use the cloud from a security point of view. This is particularly the case if you plan on doing advanced work with your online presence, such as creating and deploying applications.
Furthermore, if you are going down this route, there are further tools you can utilize to block out any malicious activity. As an example, containers are often used to simplify application build. To ensure your container security is at its best, you can use various processes and tools to keep everything safe.
16. Secure the wp-config.php file
Like other Content management systems on the web, WordPress keeps updating files to make them more secure. The WP-Config.php file is one of the most important files in the WordPress file system that contains sensitive information about your WordPress installation, including your database details, table prefix, and Secret Keys. Therefore, it must be protected from vulnerabilities. The wordPress team is trying hard to improve the system security at their end. Still, you should try to keep up to date with the latest WordPress version and keep hiding your WordPress version from crackers, and you should take additional security steps to make it more secure.
So wp-config.php file should be secure from hackers because they can find the valuable information stored in the wp-config.php file. If someone gets to access this file, he can get a website database username and password; he could log in and undo everything you’ve built! Therefore, take whatever steps you can to secure that file so that no one can access it. To do so, follow these steps:
The wp-config.php file contains Database credentials, so make them secure as more as you can; keep in mind the following tips for a secure and strong password:
- Must be at least 15 characters.
- Must be a combination of upper and lower case letters, must include numbers and symbols if your hosting company does allow to do that for MySQL database.
- Must be unique and not included names or dictionary passwords.
- You can use the Strong Password Generator: Use this strong password generator to generate secure, random passwords. It’s free. But I recommend creating your own password.
- Must be the same as your FTP, cPanel, wp-admin, database, email, or similar to any other social media account like Facebook and Twitter.
- Try to change your password frequently.
- For security purposes, never save or write your password on a piece of paper; make it secure as much as you can.
Moving the wp-config file to an unpredictable location and changing the code would create a problem every time you upgrade WordPress. So there is a better solution, create a separate PHP file in a non-WWW location, and add the WP-Config file’s location in it.
So you can change the location of your wp-config.php file from
puplic_html/wordpress/wp-config.php
to
puplic_html/wp-config.php
Protect it the .htaccess Way
Here’s the code to protect the wp-config.php file:
# protect wpconfig.php <files wp-config.php> order allow,deny deny from all </files>
After updating your wp-config.php, Change file permission (chmod) on wp-config.php to 640.
17. WordPress Security Keys and Salts
It is essential to add unique keys and salts for security reasons. There is an online secret-key service for automatic key generation. Visit this link, refresh the page, copy the keys, and paste them into your wp-config.php file.
18. Protect the wp-includes directory
To prevent someone from viewing the indexes, you have to protect the wp-includes directory; for this, you need to edit the .htaccess file.
Note: make sure WordPress does not overwrite the code below; place it outside the # BEGIN WordPress and # END WordPress tags in the .htaccess file. WordPress can overwrite anything between these tags. If you don’t know how to edit the .htaccess file, contact us, we can do it for you free of charge.
# Block the include-only files. <IfModule mod_rewrite.c> RewriteEngine On RewriteBase / RewriteRule ^wp-admin/includes/ - [F,L] RewriteRule !^wp-includes/ - [S=3] RewriteRule ^wp-includes/[^/]+\.php$ - [F,L] RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L] RewriteRule ^wp-includes/theme-compat/ - [F,L] </IfModule> # BEGIN WordPress
Important Note: this won’t work well on Multisite, as RewriteRule ^wp-includes/[^/]+\.php$ - [F, L] if you are updating your multisite, It would prevent the ms-files.php file (multisite) from generating images. You can remove this line, but it’s a security risk.
19. Swap out the upload folder
WordPress allows you to move the upload folder of the integrated media library. So you can choose any place and adjust the path in the WordPress backend under “Settings > Media library > Save uploads in the following folder.” Since the upload folder is relatively unprotected (chmod 777 – readable and writable by everyone), it should be packed, especially in cotton wool.
20. Move the WordPress instance to a subfolder
The so-called core files of the system can, of course, be placed in the main folder, but even here, you make it very easy for potential attackers since you retain the standard structure. WordPress allows swapping to a subfolder, e.g., “wp_cms4538”. You move the WordPress files integrally but leave the “index.php” in the main folder. This file has to be adapted accordingly:
/** Loads the WordPress Environment and Template */
require('wp_cms4538/wp-blog-header.php');
Don’t forget to adjust the paths to the website or blog in the backend of the WordPress installation under Settings > General.
21. Check files and Folder access Settings/Permission

Permissions are key factors in deciding who has access to what on your website. These access rights vary from ‘Read access’ to ‘Write access’ and up to execute access. Setting these access specifications correctly for different files and folders is critical to maintaining the website’s security. These permissions are specified using a three numbered value. Ideally, the file permissions for folders should be 755, and files must be 644. Permission 777 should never be used as it provides full access to your file/folder to everyone.
If your site is on Linux, you have access to your file and folder permissions through which you can choose as to who your audience will be for that particular data. You can share data with the selected audience; just make sure all your settings are not too permissive that almost anyone can access your important folders.
22. Manage WordPress Account Logins and User Permissions
A stolen password is one of the most common ways to hack WordPress. You must select strong passwords for the database, FTP accounts, professional email addresses, and WordPress hosting accounts. You can use a password manager to manage strong WordPress passwords.
Many attacks focus on admin accounts using standard methods like brute force attacks, credential stuffing, and password keylogger attacks. Always replace the default admin account and use unique usernames and passwords for each account. Also, make sure to have two-factor authentication enabled for all accounts.
If there are multiple accounts with access to the website, then use the principle of least privilege. Only grant access privileges to accounts based on the actions they need to perform and nothing more. This limits the number of things hackers have access to, should they gain entry through any one account.
23. Limited Access

Everyone mustn’t access the important pages of your site. Limiting access means that you and your potential users only access these few pages that link you to your entire site. This way, your overall site will be safe.
Secure FTP (SFTP) is a safe way of adding files to your site. The passwords in this are encrypted, so attackers cannot easily hack them.
Simple FTP is a way to quickly add up more data to your existing site, but it’s not secure. Hackers can easily interject your FTP connection.
So it’s better to use secure SFTP or SSH. Secure Shell access (SSH) can also be used to safely transfer or add files to your site.
If you are not using any FTP connection to share more files, you should delete your FTP account. Don’t leave any room empty for the hackers to try and intrude on your privacy.
24. Disable your website from appearing in directory browsing
- Disable Directory Indexing and Browsing
Hackers can use directory browsing to identify any files the admin keeps that have known vulnerabilities. Then, hackers could use this file with vulnerabilities to access the website. To disable directory indexing, you must add the following texts to the .htaccess file.
Options -Indexes
By default, if your website’s web server is unable to find a file named index.php or index.html file, a page displaying the directory contents is shown, which reveals critical information related to the plugins your website uses, posing as a security issue. To check if your website’s directory browsing is enabled, create a new folder and a text file inside that folder. Now open your directory over a web browser. In case a link to your text is displayed, directory browsing is enabled. To prevent this from happening, go to your .htaccess file and add “Options All -Indexes” to it and ensure that the wp-content/themes and wp-content/plugins folders both contain a blank index.php file in them.
25. Password on Certain Folders

You know which folders contain valuable data that might attract hackers’ attention, so it’s better that you put all such
folders on strict privacy. Keep a password on important folders so everyone does not access them.
In the control panel, go to security, then Password protects directories to see the list of all the folders. Now choose the
folders you want to keep safe and hidden from external users.
Once you have set the username and password, go to the security settings title and check the box that says “Password.
Protect this directory”. Finally, click save, and you are ready to go.
You can also find software designed for this purpose on the Internet. Download them and secure your important folders.
26. Change the prefix of the table
The WordPress users, by default, carry the “wp_” WordPress database prefix. Unfortunately, using this default prefix almost reveals your table name to hackers. Therefore, we strongly suggest you change WordPress Database Prefix.
Every table’s default name begins with wp_ like some other default features in WordPress’s database. If you don’t change it, you give the hacker a chance to easily penetrate your database tables and make changes to your site.
WordPress allows adjusting the table prefix of MySQL database tables in the current versions. This should be used urgently. The standard prefix “wp_” is, of course, known to hackers. By adjusting the prefix, e.g., in “wp45fkze_,” you make it harder for potential intruders. Also, this prefix only needs to be specified once. You don’t need to remember the prefix anyway.
So if you modify the tables’ names to some customized words related to yourself, it will be less accessible to the hacker.
27. Database Name
Similarly, the name of your database is also by default ending with a widespread name. Assigning it some new name or adding a unique alphabet sequence to it will make it stand out. This way hacker will find difficult to decode it. You can take help from certain software to automatically change the database’s name to some unique username.
28. Use HTACCESS to increase security
An Htaccess file is a potent instrument. Via “.htaccess,” numerous security settings can be made which restrict access to numerous important configuration files and backend areas.
We recommend the WP HTAControl plugin. Using this plugin, numerous security settings can be activated with a few clicks:
- Securing the “wp-config.php” file against access from outside
- Securing the “comments.php” file from outside access
- Limitation of the upload limit (e.g., to 500kb)
- Deactivation of the “indexes” WHERE id =, i.e., the automatic listing of a folder content with the direct call
- Deactivation of server signatures in case of error messages (in order not to give important server information to attackers)
- Own entries in the .htaccess file
- Numerous settings have a direct influence on the “spit out” URL.
… and much more
29. Lock WordPress backend “WP-Admin” via IP
If, for example, a so-called “fixed IP address” is used within a company, access can be restricted to exactly this address. If you access the backend of WordPress outside this IP address, you will receive an error message (“Forbidden”). This way, the administration area can be protected extremely effectively, but this requires that you always access the website via the same IP address. Private ADSL providers (access from home) rely on “dynamic IP addresses,” which can change quickly. If, in this case, only certain IP access is granted, the bulkheads are sealed after 24 hours at the latest.
This restriction on the IP address is interesting, for example, for companies that host their website on their own in-house servers and therefore only need to have access from there for day-to-day maintenance.
To set up this IP block it is sufficient to put a ".htaccess" file in the wp-admin/ folder with the following content (whereby the corresponding IP address must of course be adapted): AuthUserFile /dev/null AuthGroupFile /dev/null AuthName "WordPress Admin Access Control". AuthType Basic <LIMIT GET> order deny,allow deny from all # whitelist IP address allow from 89.123.57.12 </LIMIT>
30. WordPress Backup
It does not matter how protective you are; your website still has a chance of being hacked. So, it is wise to keep a backup. You can use many paid and free WordPress backup plugins to keep your backup. In addition, you can use cloud services (remote locations) like Dropbox and Amazon to save full-site backups regularly.
Always keep in mind to have your website backed up.
If ever your site gets hacked or you make some changes in the software that are irreversible, the best thing you’d want is an entire copy of your original website.
Yes, that will be a sigh of relief as you know you have all the databases and files necessary to regenerate your site. This way, if someone breaks or hacks your site, you can start fresh, recover all the data, and report/delete the previous site.
But for all this, you need to have a backup and make sure the copy is regularly updated with all the productive changes you make on your WordPress site.
You should save the copy of your entire site at two different places other than your email (which might get hacked too).
The best option is to keep a backup in the cloud or your OS. This will ensure that even if anything goes wrong, you have an extra copy in hand. Here is a list of the best WordPress backup plugins.
31. Run scheduled malware scans
Scheduled malware scans help you to stay ahead of malware infections. You can use different plugins to run scheduled malware scans. But, stay alert while downloading plugins; the unauthorized source of plugins can cause security issues.
32. Activation of Web Application Firewall (WAF)
Enabling a Web Application Firewall (WAF) is advantageous. The activated WAF blocks malicious and suspicious traffic before they reach the website. In this case, we also ask you to select the best quality security providers like Sucuri.
33. Automatically log out Idle Users.
The idle User Logout plugin can use to log out when the site is idle, and the user is not working. With this plugin, you can set an ideal time, after which the site is automatically closed.
34. Disable XML-RPC in WordPress
The XML-RPC is a popular plugin connecting WordPress sites with the web and mobile apps. On the other hand, XML-RPC can also cause brute-force attacks. While XML-RPC is active, the hackers can use hundreds of passwords by using the system.multi-call function. Therefore, we strongly recommend disabling this feature.
35. Add Security Questions to WordPress Login
This simple but effective method makes it harder for hackers to hack your website. You can set a security question with the help of the WP Security Questions plugin. It would help if you did not ask any question which has an obvious answer, and the hacker can easily find it. Instead, offer personal and odd questions to perplex the hacker.
36. Quality Hosting is Important
Whether you want to design a one-page website for your specific product or are about to build multi-page business websites, quality hosting should be one of your major concerns as it can work as an extra layer of security for your digital asset.
Most of us ignore this part because all we need is cheap hosting and a cheap domain. Quality is essential because you can’t buy something. That is the main reason your site is unsafe.
If you have reliable hosting, it will maintain your performance and make your website even faster. Best hosting companies offer lots of features that help you to rank on the search engine as well.
Ensure your hosting offers 24/7 support because if some problems occur, you can contact them immediately to get the necessary support.
Quality hosting is an essential factor in keeping your website secure because it automatically updates your website in case of any malicious activity.
Web Hosting affects Security.
Before you even work on your website, you must pay close attention to your host provider. Even though it can be tempting to try and find the cheapest option on the market, you should avoid this approach. Instead, your focus needs to be on the quality of the provider and the hosting package you select.
At the very least, you should opt for dedicated hosting over shared hosting, although if you want that extra layer of protection and are willing to pay extra, cloud hosting is the best pick available.
Most people see web hosting as a necessary part of doing business. They understand that they can’t get their website on the Internet if they don’t have web hosting. But from the standpoint of many, all web hosting is created the same. So they are happy if they are not paying too much money for web hosting and their site is up and available when they go online.
Many people do not understand the far-reaching consequences their choice of web hosting will have on their website’s performance, the site’s security, and the long-term reputation of their business. Good web hosting is an excellent investment. It offers a quantifiable, tangible, long-term return on investment.
Suppose the web hosting provider you choose is not reliable. In that case, your business is going to struggle with inconsistent performance, unwanted downtime, and security issues that could put your private data and the personal data of your clients at risk. For example, if you had a customer who wanted to purchase something from your e-commerce store but could not complete the transaction because of a security glitch or a glitch with the web server, you would lose that customer forever.
Appreciating the Link between Web Hosting and Security
According to Clark School’s study at the University of Maryland, a hacker attack occurs every 39 seconds in the US. Small businesses are usually an easy target for hackers because their cybersecurity infrastructure is not nearly as hackerproof as it is common for some more prominent companies. Securing your company properly costs a lot less than a data breach.
When most people think about online security, they think about services like a VPN. And it’s true that when used properly, a good VPN can boost your company’s online security by encrypting and creating a secure tunnel for the data you are transmitting over your network. However, your web hosting service plays an even more valuable role in keeping your business and website safe. It all starts with choosing a secure web hosting solution for your company.
First, you need to understand that regardless of your business’s size, some cybercriminals and hackers want to get access to the data on your website. Small businesses are not immune. They are a favorite target of cybercriminals and hackers because most lack the security protocols you would find with larger organizations.
For this reason, it is essential to take critical steps to guarantee that your web hosting provider is giving you the best security measures to protect your site. This includes getting rid of malware and having other scanners to identify and eliminate malicious code that hackers need to introduce.
A good web host provider will have an effective policy that protects you from distributed denial of service attacks. A distributed denial of service attack can render your website useless. By bombarding your side with so many fake visitors, it can slow things down where legitimate visitors cannot access your site. Your web host provider is key in guaranteeing that your hosting system is accessible even if there is a cyber-attack.
Few things are as frustrating as having your website hacked and then losing all of your data. The implications for an online business are catastrophic. A data breach and data loss at this level could put your business out of commission permanently. Here again, is another reason it’s important to know what your web hosting provider is doing to protect your data and how they are backing up your data.
You should inquire about what data is being backed up. You should know how frequently the hosting provider is backing up the data. And you should know where that backed-up data is stored. You should have unfettered access to that data and the ability to restore your website from the backup seamlessly.
To sum this up, any cyberattack, from malware to a potential data breach, should be considered so that you can protect your data the best way possible. Your web hosting provider should prioritize security above all.
Things to Consider When Choosing Shared Hosting
You are likely starting to see that web hosting has a tremendous impact on your website. If you choose the wrong hosting, you could leave your site open to exploitation. You could put your site at risk.
This is often the case when considering shared hosting. Shared hosting is popular because it’s cheap. And many businesses, when they first start, are looking for the lowest cost option. But there are so many drawbacks to security.
Shared hosting works because multiple sites share the same infrastructure. And that’s where all the problems start.
From a security perspective, shared hosting can open up your site to be exploited by something from another site sharing the same host with you. Shared hosting means that someone else’s mess could affect you. If there is another site on your server that has weak security measures or if they fail to update plug-ins regularly, you will probably suffer the consequences, including shutdowns, code injections, and cyber-attacks. The lack of isolation seen on shared hosting can undo all of your best efforts to keep your site secure, safe, and strong.
Your Hosting Provider Can Make Your Online Security Easy or a Challenge
Keeping your hosting secure can be a time-consuming task. The amount of time it consumes depends a great deal on what company you are using as a hosting provider and the hosting plan.
If you choose a cheap shared hosting provider, your security could be a nightmare. On the flip side, a great private hosting provider, such as those offering dedicated hosting or a VPS, can make security a dream. Most web hosting companies offer services that are somewhere in the middle of the two extremes.
Finding the right hosting provider is going to take some time. It is worth it for you to put thought into how you want to manage your website security.
If you decide to use shared hosting after looking at all the pros and cons, putting a little effort into the search process may lead to you finding a plan and a vendor that works for your security needs. The key is to ask the right questions going in.
- What will you do to help me keep my website secure?
- How will you respond if my website is defaced or exploited?
- What denial of service protection do you offer?
- What is your policy for handling backups? How easy is it to restore backups?
Getting the answers to these simple questions can help you determine if the web hosting company manages security in a way that’s right for you. This is the only way you will find a provider that will keep your site as secure as you want it to be.
Two Factor Plugins
Activation of two-factor authentication is one of the best ways to minimize brute force attacks. In the two-step or two-factor authentication mode, apart from the password, your WordPress will also ask for an OTP (one-time-password), which will send to a specific phone number.
Two-factor authentication refers to the two-way process through which the website has to pass. This process takes a little more time and keeps the business website even more secure.
First, you will enter the username and password. Then a unique code will be sent to your device that you will have to provide to start using the website.
This factor is easy to add with the plug’s help and plays an important factor in keeping the business website more secure.
If you are using this process, add the correct number because adding the wrong codes will block the website.
With WordPress plugins, you can add a second level of protection to your blog and can give additional protection to your WordPress sites with the latest version. You can use these plugins while login in from your mobile devices and via email or SMS.
I found these plugins for securing your WordPress site; check out the following plugins:
– SimpleAuth: Very Simple Secure Login
SimpleAuth is a simple and secure multi-user PHP login system. No database is required—no PHP knowledge is needed to implement this login system. You can secure all kinds of pages: customer area, administration interface, member page, or private page.
Vladimir Prelovac:
I expect plugins like this to rise in popularity soon or even become a part of the core. We are soon adding similar support to our ManageWP.com users as well.
– Login LockDown
Login LockDown records the IP address and timestamp of every failed WordPress login attempt. If more than a certain number of attempts are detected within a short period of time from the same IP range, then the login function is disabled for all requests from that range. This helps to prevent brute force password discovery. Currently, the plugin defaults to a 1-hour lockout of an IP block after 3 failed login attempts within 5 minutes. This can be modified via the Options panel. Administrators can release locked-out IP ranges manually from the panel
WordPress Security Plugins
The use of WordPress security plugins is widespread but a helpful step. With good WordPress security plugins, you can easily avoid significant security threats and malware. The Sucuri scanner (WordPress plugin) has also gained popularity.
Plugins are one of the things that help make WordPress so versatile. There are thousands of security plugins for WordPress, and each comes with its own set of features. Sorting through them all would take too much time, so do some research to find the best ones.
Keep in mind that there are different kinds of security plugins and most websites need more than one to stay adequately protected. Vet each properly before installing it, though, because mobile phones can be fake or compromised, just like with apps on mobile phones. Take a look at user reviews, install base size, and the vendor’s terms of service before installing a theme or plugin.
- iThemes Security – Scans your WordPress installation for security vulnerabilities and suggests corrective actions.
- Semisecure Login Reimagined – Semisecure Login Reimagined increases the login process’s security by using a combination of public and secret key encryption to encrypt the password on the client-side when a user logs in.
- Login LockDown – Login LockDown records the IP address and timestamp of every failed login attempt.
- WordPress File Monitor – Monitors your WordPress installation for added/deleted/changed files. When a change is detected, an email alert can be sent to a specified address.
- Stealth Login – This plugin allows you to create custom URLs for logging in, logging out, administration, and registering for your WordPress blog.
- Limit Login Attempts: a useful plugin that allows you to limit the number of tests you can log in to the WordPress system. This is a plugin that allows you to ban IP through cookies or users and prevents it from brute force by a single subject.
- Askimet: perhaps one of the most popular WordPress plugins allows to manage better the comments that have spam, classifying them and preventing them Rinser of new bots.
- YES, Antispam Captcha: always to protect the login page, this plugin puts a captcha on the page to be sure that access is always groped a human and not a botnet.
- Antivirus: Another plugin responsible for checking the files in our installer is looking for any malicious code.
What to do if hacked?
In case your website is compromised, stay calm. First of all, try to reset your admin password and scan your website for malicious content; try to contact your host to put everything back to normal. We also provide professional WordPress Security services to remove malware and fix the hacked site.
WordPress Security is a Never-Ending Job
If you have a WordPress website, you must consider its security issues sincerely. Many features of WordPress make it vulnerable to hackers. However, by taking several precautions and using appropriate plugins, the vulnerabilities could be reduced.
There’s no way to eliminate threats. Website security – and cybersecurity in general – is about reducing risk as much as possible. That means deploying multiple security methods and precautions to keep threats at bay.
The threats keep developing as criminals get more sophisticated. However, website admins need to make sure their protection methods stay current.
Conclusion
In conclusion, we can say that we now have an added security layer to protect WordPress. Still, much of what is done must be on hosting providers, especially in your server’s configuration, so ensure that the provider’s servers are tested to host WordPress. There are the necessary security measures at the system level.
Cybercrime has increased exponentially over the years, with most of the data being stored in online datastores, which makes it essential to try and be one step ahead of the cybercriminals. So, proceed with some of the above ways to make advance the security of your WordPress website.
Keep in mind that while this checklist covers all the basics, it isn’t a full WordPress security guide. WordPress admins should regularly consult WordPress security resources to ensure their security habits stay up to date. This checklist can also be consulted now and then to ensure that all the essentials are still covered.
These are some of the very basic yet little extra effort-requiring methods you can use to secure your website. However, more methods that require more effort also exist, and they can go pretty far up when it comes to securing your websites, but it is important that most of the measures mentioned above can be performed.
Try the suggestions we listed for you. If you like our tips, stay tuned for further updates!




