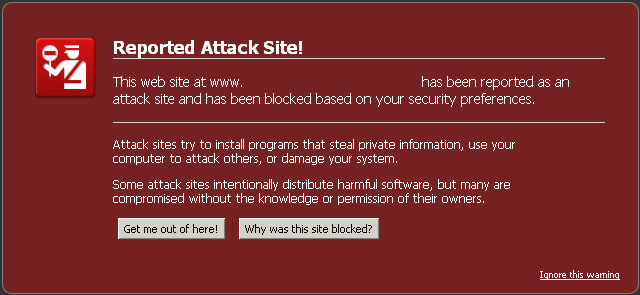
As a web designer, my small design studio’s portfolio site is my most valuable asset. It serves as a lead generator and a sales tool. But a few weeks ago I discovered something very disturbing. When checking my site’s current rankings, I was greeted with this friendly little Google disclaimer:
What does that mean? How could this have happened, and more importantly, how do I fix it? After doing a bit of digging, I discovered that my WordPress site was hit with what is referred to as the “Pharma Hack”. It’s a complicated scam, but hackers got into my WordPress admin area and inserted some code that would generate backlinks to various less-than-reputable online pharmacies. The most frustrating part is that it is undetectable to the average user, and only search engines can see it happening. This makes the problem very hard to diagnose and fix. The fact that I’m a non-coder only exacerbated the problem. In short, I had no idea where to start. So I went with my first instinct, which was to throw money at the problem simply.
Hire an expert.
I went onto elance.com and posted a job looking for somebody who had the experience necessary to quickly find the problem, fix it, and report that it is fixed to Google. I found someone who had glowing recommendations and claimed to have fixed many same issues in the past. He even boasted a 100% success rate.
So what did he find? As it turns out, nothing much. He ran some sort of automated program that is supposed to scan for malware on the site, and it came back with nothing. Rather than digging deeper, he simply called the job complete and told me to resubmit the site to Google, saying that it’s completely clean. Well, I did, and nothing changed. The disclaimer remained. With no confidence in the “expert” I had hired,
I decided to take matters into my own hands.
I put on my detective hat and did a few internet searches based on the disclaimer and the website that was linked to in the spammy code and found someone with the same problem I was having. Following links provide great help:
- How to Protect Your WordPress Website from a Pharma Hack
- Identifying, Removing, and Preventing Malware on Your WordPress Site
It showed me which file the spam code was inserted in, and I removed it myself. I have to admit; the fact that I, a complete coding-novice succeeded where a so-called “expert” had failed was a nice little victory for me. It almost made me forget that I was out $150 that I had to pay him.
Once the offending code was cleared out, there was still some remaining work to be done. First of all, I had to…
Resubmit my site to Google.
This involved simply adding a WordPress plugin that would generate an XML sitemap of my entire site that I could then submit to Google using Webmaster Tools. From there, it’s just a matter of time before Google recrawled my site and discovered that it was now spam-free. It took several weeks for the disclaimer to drop off of all the pages, in truth, there might still be a few deep links that still have it, but my main landing pages are now free and clear.
But just to be safe, there were a few more things I needed to do:
I changed my usernames and passwords.
This went for both my FTP access as well as my WordPress admin area. I found out that WordPress sites that use the default username of “admin” are hardest hit by this type of hack. And of course, that’s what I was using. I changed that to something more custom, as well as my password, with the goal of making it as secure as possible. This includes a mix of capital letters, lowercase, numerals, and symbols. And here’s a tip if you want to be extra safe: Don’t let your browser store your password for you. Hackers can access this information as well, and use it against you, so just make it something strong that you can easily memorize.
I moved my site away from GoDaddy.
From what I have read online, and from what my web developer told me. Apparently, this sort of hack happens most frequently on GoDaddy-hosted sites. This has to do with a vulnerability that exists within their framework, and worst of all, they don’t provide any support for this type of thing at all. They usually just blame it on WordPress and leave you to figure it out for yourself. So it didn’t take me much convincing to pick up and move on to greener pastures.
Best Options for hosting WordPress sites.
Main Takeaways:
- Don’t use “admin” as your username. Come up with a customized username that will be harder to figure out.
- Use strong passwords. Include letters, (both upper and lower-case,) numerals and symbols.
- Don’t save your passwords when prompted. Use a strong password that you can easily remember.
- Find a good web host. GoDaddy is notorious for being hacked into and doesn’t provide much help in fixing it when it happens.
Face it, sometimes this kind of thing happens. But there are things you can do to help prevent it, and take it from me; prevention is much easier than fixing the problem after the fact.







you pay those $ 150 ‘expert’?
If you serious about security and business.. than its worth to pay
I would first try to retore the site from the cpanel. This a good reminder of how important is to backup your site